
Cybersecurity services to keep your business moving forward.
Fortify your company’s defenses against cyber attacks and breaches with the right set of solutions.
Defend your digital space.
All businesses need to manage cyber risk, but small and mid-sized businesses have everything to lose if those risks become reality.
Improve your security posture with practices, technology, and support designed by the cyber security and risk management experts at Periculus.
- Help prevent cyberattacks
- Meet compliance requirements
- Elevate your customer confidence
Cybersecurity Services
Business Grade VPN
Virtual Private Gateway
Employee Security Awareness Training
Phishing Simulation
Website Vulnerability Scan
Next-Gen Antivirus
Managed Services Support
Dedicated IP Address
FAQs
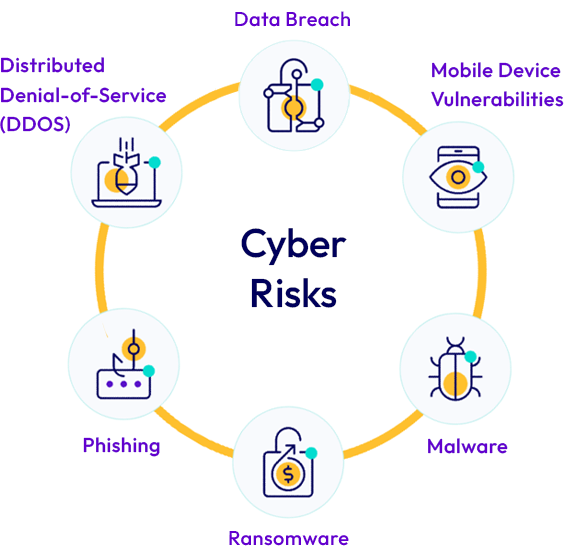
Managing cyber and overall business risks may not be at the top of your to-do list, but it is arguably one of the biggest threats to the sustainability of your business. Even if you don’t believe you’re at risk for a data breach, hackers would beg to differ. In their eyes, all information is valuable, and soft targets, like many small and medium-sized businesses without protection, provide an easy target.
Having and using a suite of solutions to minimize your risks offers a layer of protection that makes a hacker’s job more difficult.
Data privacy should be a top concern for any business. Keeping the personally identifiable information (PII) of your employees and paying customers safe is an expectation every consumer has in the digital economy. If you’re not actively evaluating and working to minimize your risks, your business and its reputation are more likely to suffer should an event happen, leaving you with the difficult task of explaining why you chose not to protect your customer’s data, or your own data.
Once your payment is processed, some services are immediately activated, while others require further steps for activation to be completed.
From purchase to launch, we advise customers to expect 1 – 2 weeks to get fully up and running and 2 – 3 months to get fully comfortable with the services.
Through Periculus Cyber, businesses can access powerful mitigation services and tools to protect their companies. If your business purchases a services package on Periculus Cyber, you will have access to customer service agents and may have direct consulting services included, depending upon your package. Our agents and IT consultants will do their best to answer any questions you may have.

Get ahead of risk today.
Enroll now in a cyber security program or reach out to discuss your situation.